Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences
![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)
In the previous article, we discussed the theories behind symmetric and asymmetric encryption. Now, let's explore how these encryption methods are used in real-world scenarios.
Imagine Alice needs to send a secret message to Bob through an unsecured channel, and Bob also needs to send a reply. So, let’s understand how they can utilize symmetric and asymmetric encryption for secure communication.
Using Symmetric Encryption…
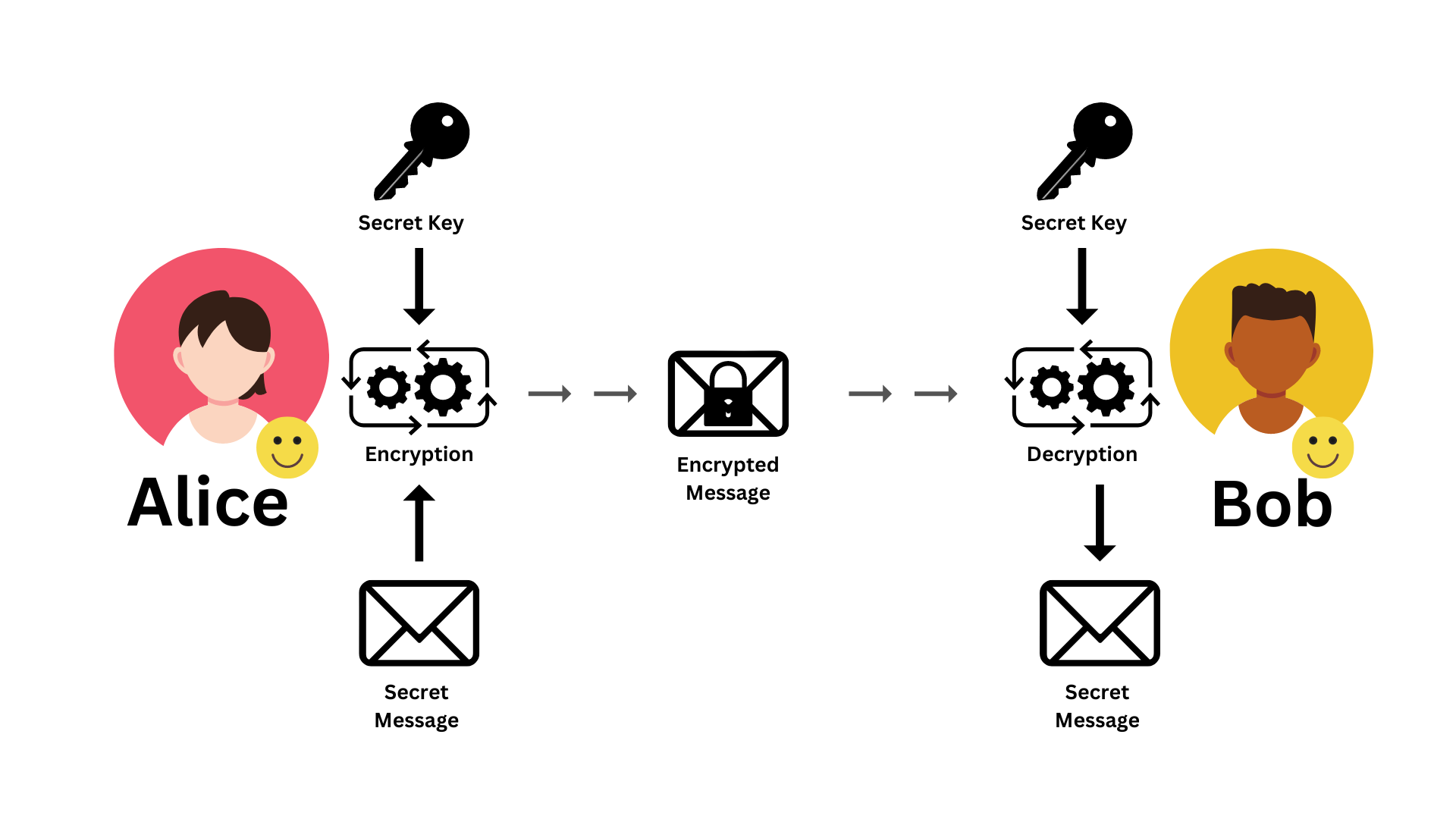
Diagram 01: Symmetric Encryption | Message from Alice to Bob
So, in this section we’ll discuss how they could utilize the symmetric encryption schema. As a prerequisite,
- Both parties need to agree on the symmetric encryption algorithm.
- Next they should generate an appropriate encryption key.
- They exchange this key securely, ensuring it remains confidential and inaccessible to unauthorized individuals
Once all the prerequisites are fulfilled, Alice can send her the message as seen in Diagram 01
Step 01: Alice encrypts her secret message with the agreed symmetric encryption algorithm and key.
Step 02: Then Alice sends the cipher to Bob through the unsecured network.
Step 03: Bob receives the encrypted message. And he uses the same secret key to decrypt the message and obtain the original message from the received cipher text.
This ensures the successful transfer of the message, illustrating how Alice can securely communicate with Bob.
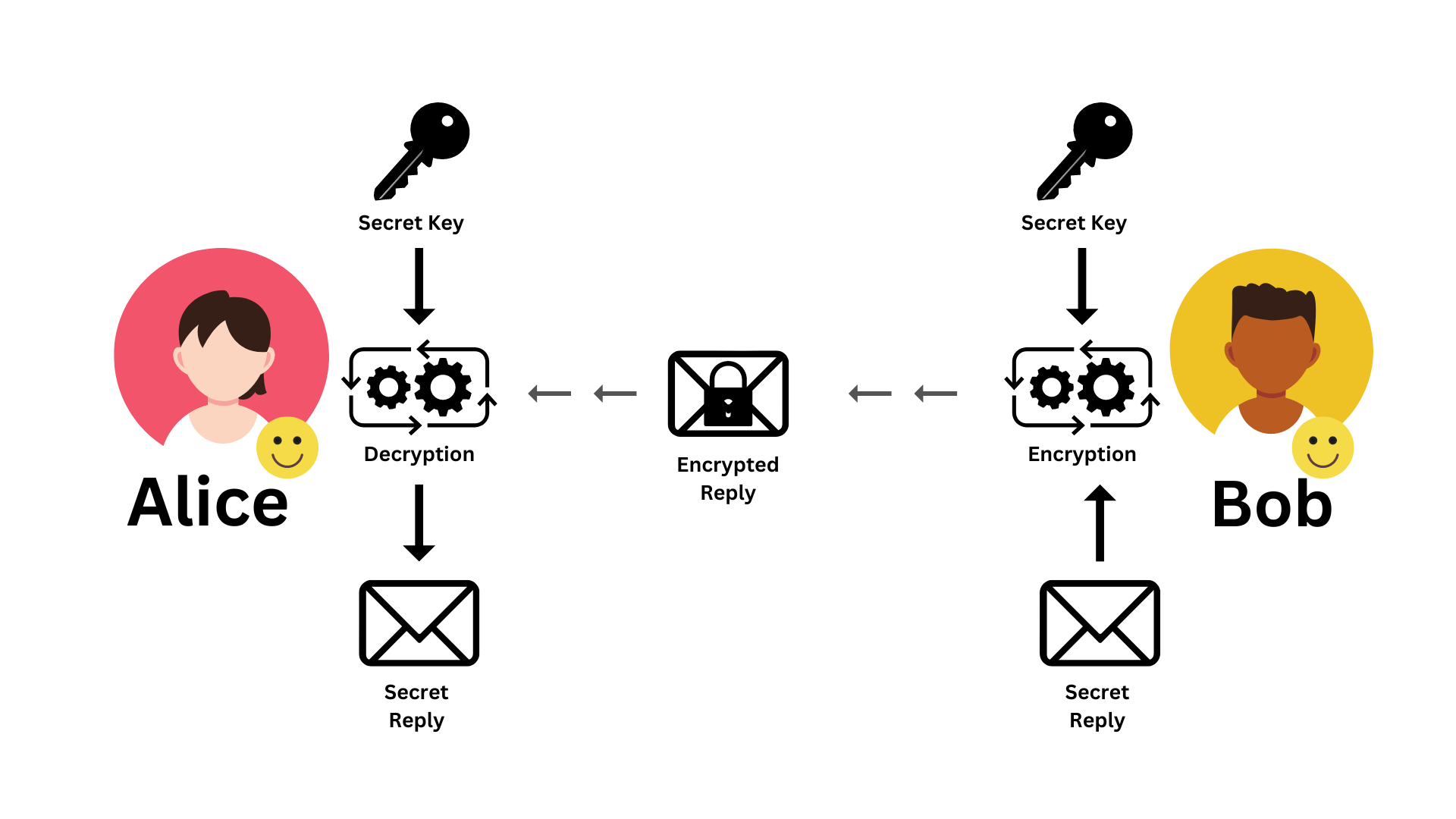
Diagram 02: Symmetric Encryption | Reply from Bob to Alice
Next, Bob needs to respond to Alice (refer to Diagram 02). They continue using the same key for this exchange. The process is straightforward and mirrors the previous steps in both directions. The only difference is that this time, Bob encrypts the message, and Alice decrypts it. Rest assured, the message is securely sent back to Alice.
Using Asymmetric Encryption…
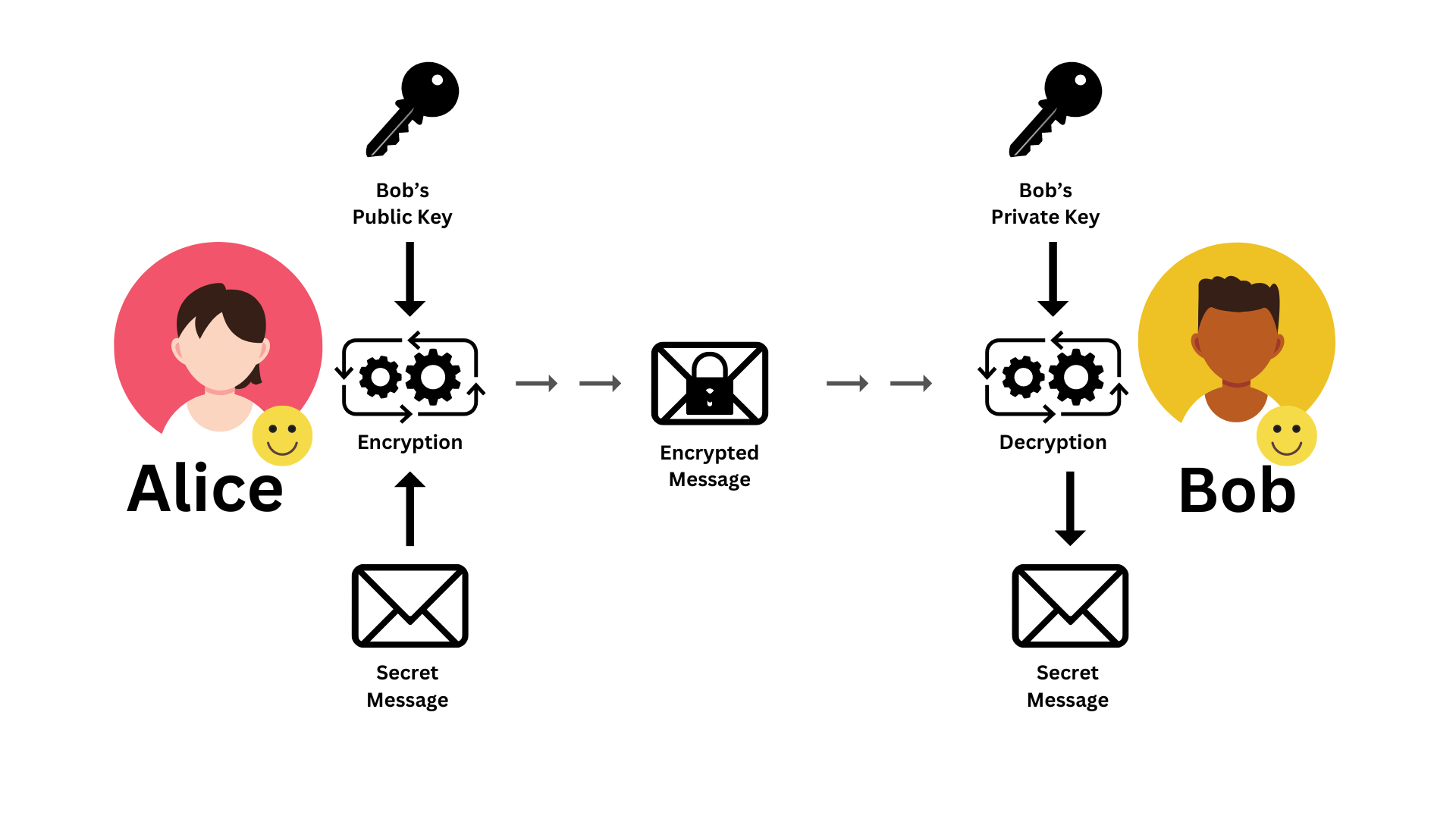
Diagram 03: Asymmetric Encryption | Message from Alice to Bob
In this section, let’s discuss the process of utilizing the asymmetric encryption. As a prerequisite,
- Both parties should agree on the encryption algorithm.
- Both parties should generate their public-private key pairs, and it’s their responsibility to keep the private key secret, without exposing it while the public key is freely available to anyone.
Once all the prerequisites are fulfilled, Alice can send her message (Diagram 03).
Step 01: First, Alice gets Bob’s public key and encrypts the secret message with the key.
Step 02: Then Alice sends the cipher to Bob through the unsecured network.
Step 03: Once Bob receives the encrypted message, he can decrypt the message with his private key.
The message was successfully transferred, and only Bob can read it since he is the only one who has the private key. That’s how Alice can send a message to Bob securely.
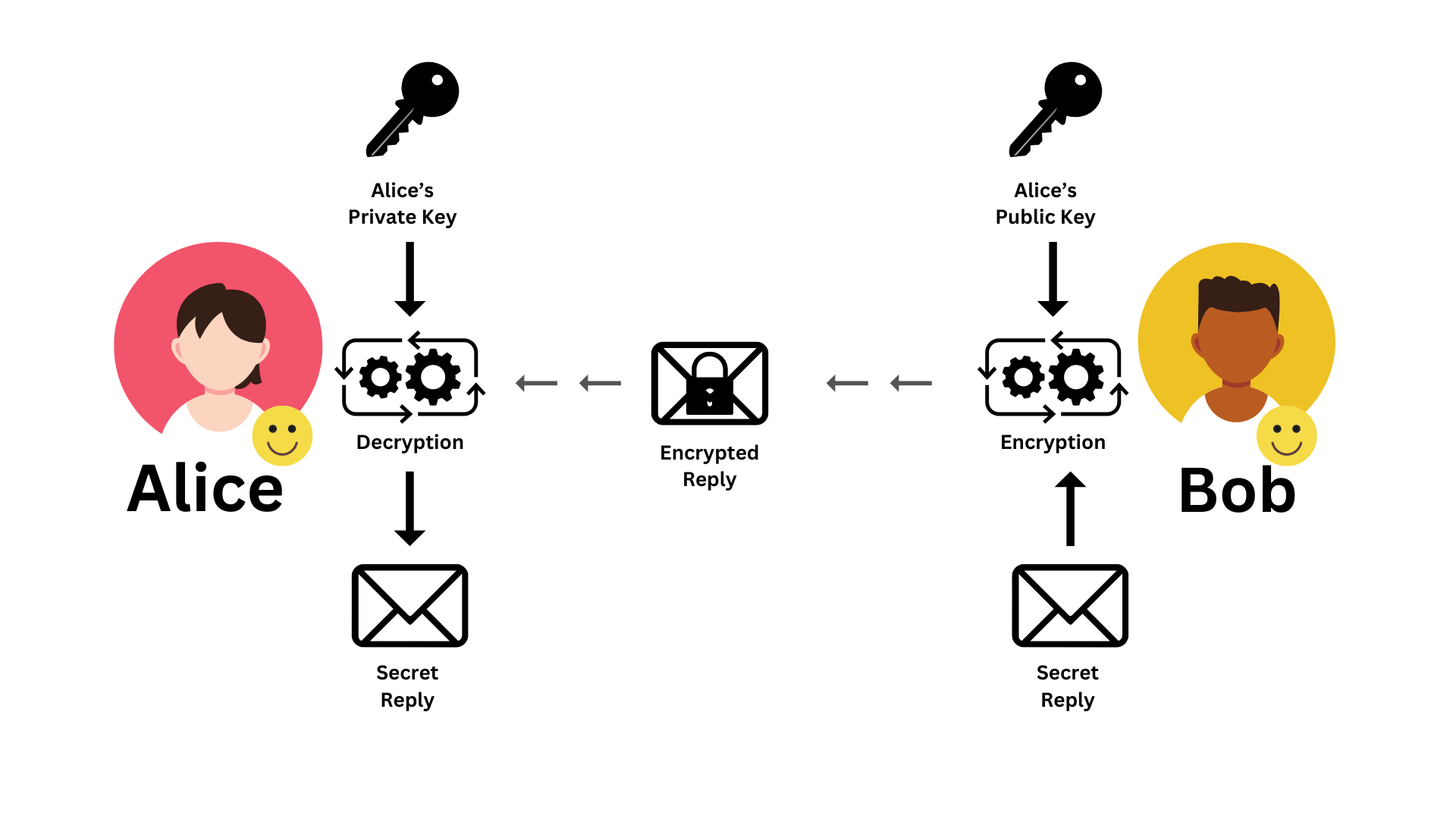
Diagram 04: Asymmetric Encryption | Reply from Bob to Alice
Next, Bob needs to send a reply to Alice (Diagram 04). The steps to send the reply are as follows.
Step 01: In this scenario, Alice will receive the reply. Therefore, Bob retrieves Alice's public key and encrypts the response using it.
Step 02: Then Bob sends the cipher to Alice through the unsecured network.
Step 03: Once Alice receives the encrypted reply, she can decrypt the reply with her private key.
As a result, Alice securely receives the reply. As you can see, unlike symmetric encryption, bidirectional communication with asymmetric encryption introduces complexities and differences in managing keys.
Coming Up Next…
In this article, I hope you've gained insight into how symmetric and asymmetric encryption play crucial roles in securing data communication in real-world scenarios. As we've explored in our previous article, both approaches come with their own set of pros and cons.
To address these practical challenges, there’s a solution that combines the strengths of both techniques. What's the solution? Let's delve into the concept of Hybrid Encryption in our upcoming article.
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
 27 May 2024
27 May 2024