Hybrid Encryption: Utilizing Symmetric and Asymmetric Encryption for Enhanced Protection
We already discussed encryption and the symmetric and asymmetric encryption schemas in the previous articles. It also discussed the advantages and disadvantages of each schema. Even though encryption plays a vital role in safeguarding sensitive data from unauthorized access, sticking to a single encryption schema can be vulnerable in your use case, and also, it may not be the best option you are searching for.
As an example, let me explain a simple scenario. Think that Alice and Bob need to communicate securely. So conventionally, they have to choose either symmetric or asymmetric schema.
Communicate With Symmetric Methods…
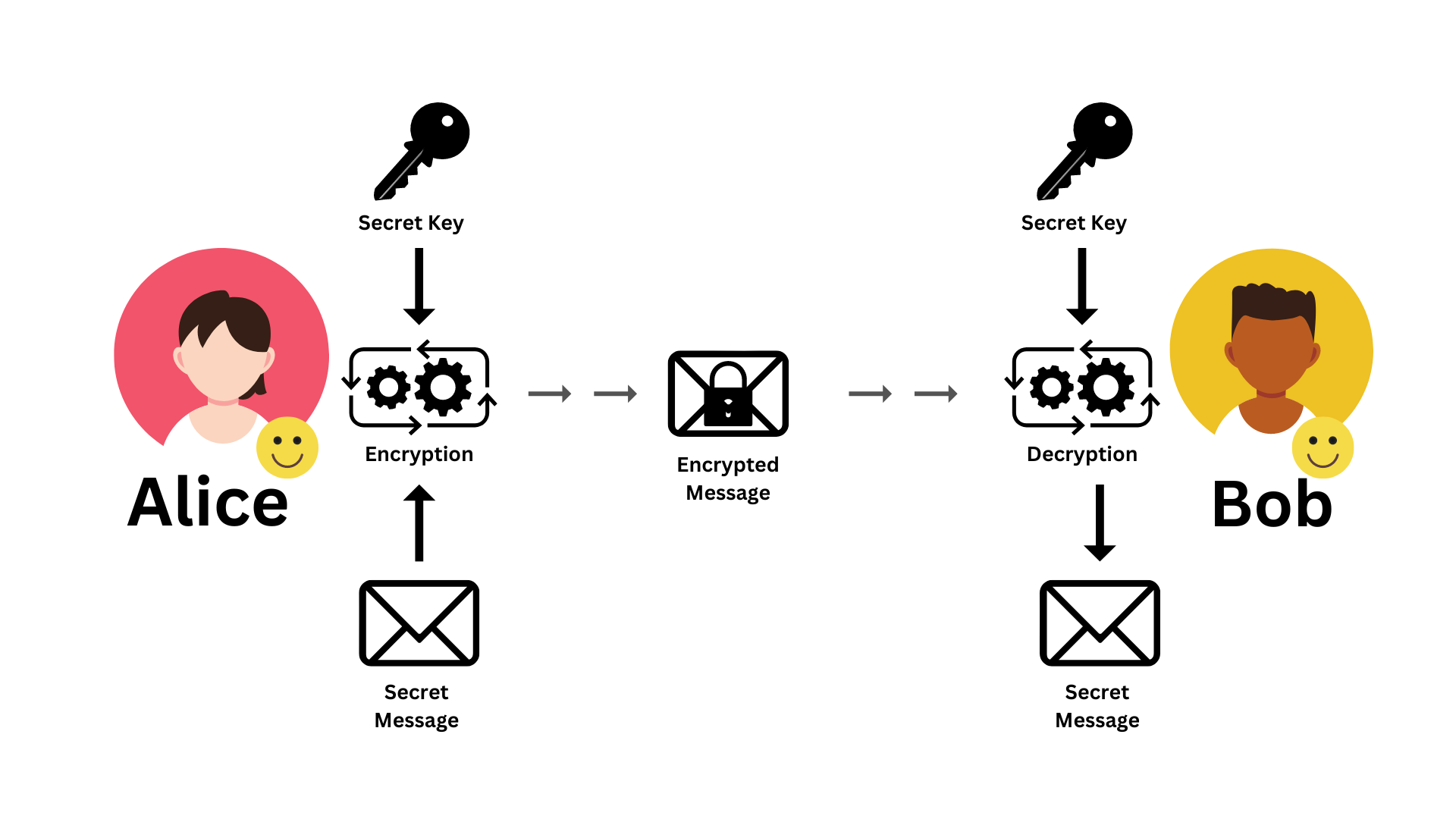
Diagram 01: Symmetric Encryption
We discuss the complete process in the previous article. In summary, first, they have to generate the key and share it. Once the key is shared, they can start their communication. This means Alice can send messages to Bob and Bob can send messages to Alice as well. The process is straightforward and similar in both directions.
But, the main issue we face there is the key sharing problem. They need to communicate securely since they have to communicate through unsecured channels. When it comes to key sharing, they still face the same issue, how could they share the key securely, without compromising it?
Special Note: To avoid these kinds of issues, there is a cryptographic solution called the key exchange method, that allows two parties to generate the same shared secret key over an unsecured channel without exposing the secret. We’ll discuss these methods in the future.
Communicate With Asymmetric Methods…
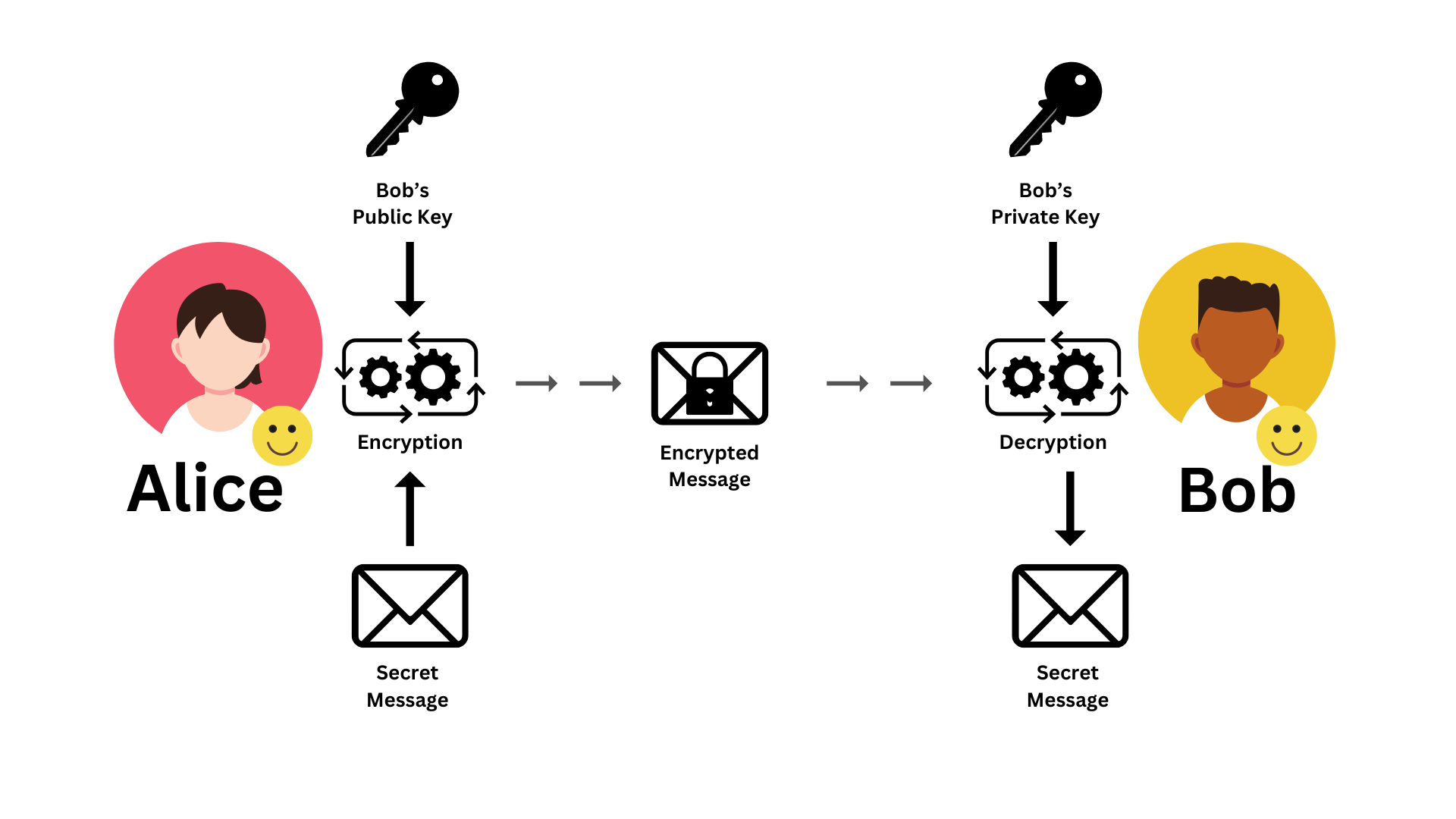
Diagram 02: Asymmetric Encryption
The other available schema for encryption is asymmetric encryption. In the previous article, we deep dive into that process as well. In summary, as a prerequisite, both Alice and Bob should have their key pairs. And they should keep the private key secret, without exposing it, while the public key is freely available to anyone who wishes to communicate with them.
When Alice sends a message to Bob, Alice has to find Bob’s public key. Then she can encrypt the message with Bob's public key and send the message to Bob and Bob can decrypt the message with his private key. And the other way around, Bob has to encrypt with Alice’s public key and send it to Alice, so that only Alice can decrypt it.
The main issue we have with this method is that it uses more resources, and also it takes more time than the symmetric method for encryption and decryption processes. So when it comes to big data and time-sensitive communication, there is always a delay and a cost.
Hybrid Encryption Into the Picture…
Even though the term “Hybrid Encryption” feels odd, it’s not rocket science. It’s all about how we utilize both symmetric and asymmetric encryption at the same time for secure yet effective communication. As a prerequisite to communication, both parties should have their asymmetric key pairs, and as usual, the public key should be freely available and the private keys should be kept secret.
So, let’s take the regular example of Alice sending a message to Bob. The process can be divided into two sections, Session Initialization and Secure Communication.
Session Initialization
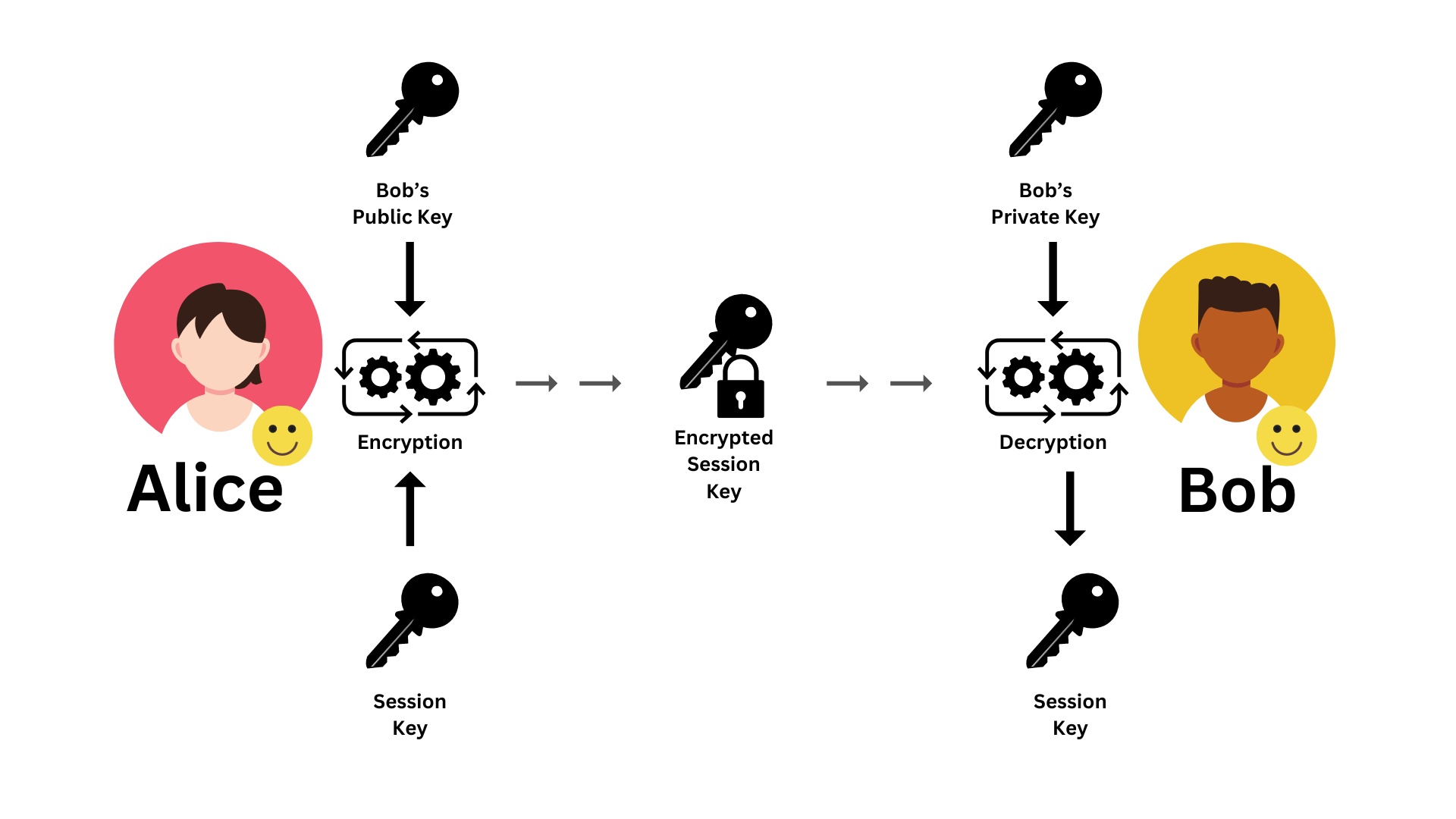
Diagram 03: Hybrid Encryption | Initiating Session
Let’s talk about the session initialization. In this stage, both parties have to initiate the session and share the session keys. For that, they use asymmetric encryption. The steps are as follows.
Step 01: Alice decides on a symmetric encryption algorithm and generates an appropriate encryption key. (This key is temporary and only used for this encryption session. So it is also called a session key.)
Step 02: Then Alice gets Bob’s asymmetric public key, and encrypts the session key with that key. And sends the encrypted key to Bob.
Step 03: Once Bob receives the encrypted key, he can decrypt it with his private key and get the original session key.
So that way, Alice and Bob shared the same session key without exposing it to a third party, securely using asymmetric encryption. So we say, the session is successfully initiated.
Secure Communication
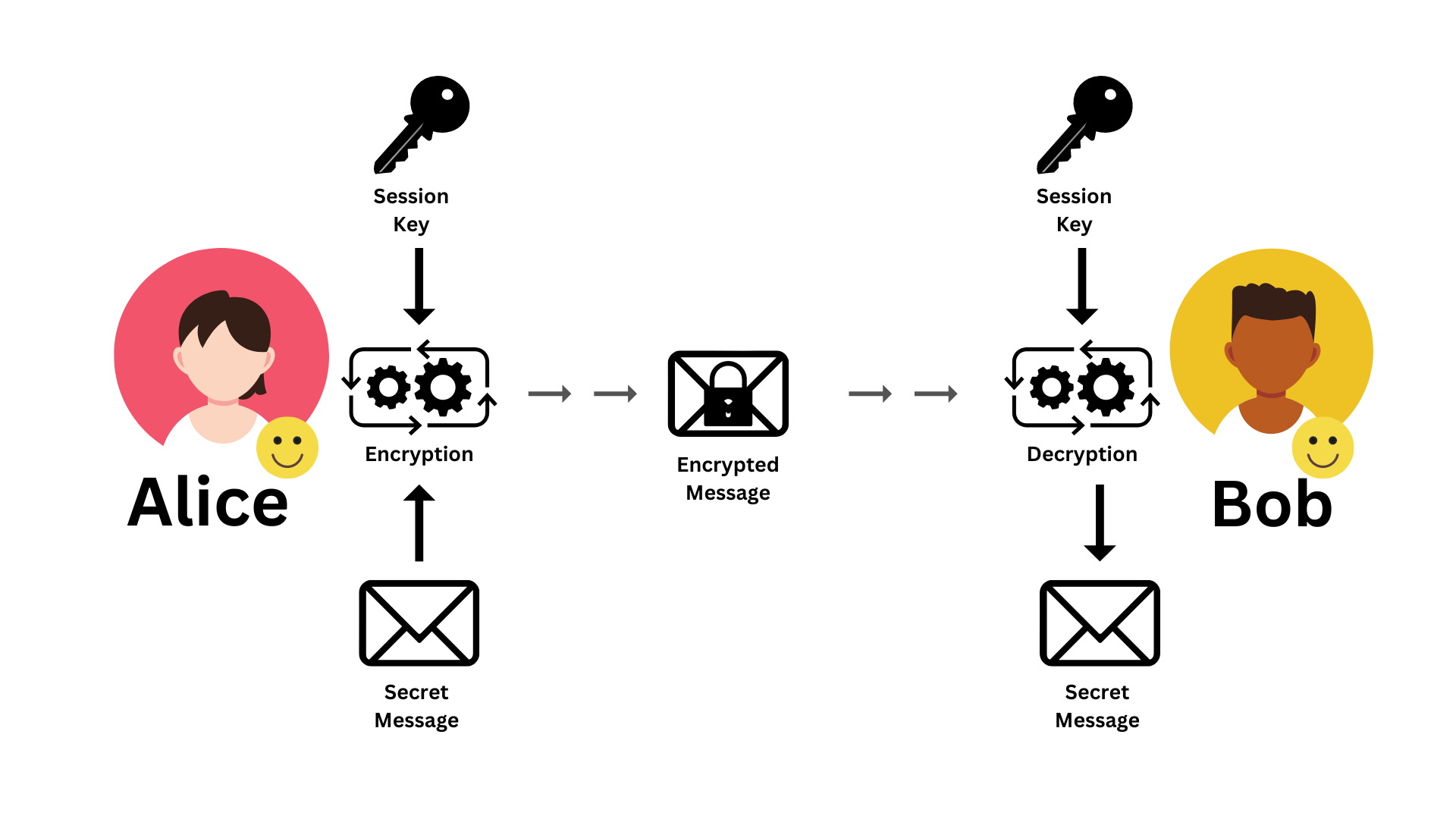
Diagram 04: Hybrid Encryption | Message from Alice to Bob
Now they have a secure tunnel between them. So any of them can send messages to the other party using the tunnel. The process is simple. First, consider the process where Alice sends a message to Bob (Diagram 04).
Step 01: Alice encrypts the message with the session key and the chosen symmetric encryption algorithm.
Step 02: Then Alice sends the encrypted message to Bob through the unsecured network.
Step 03: Once Bob receives the encrypted message, he can decrypt it with the session key and get the original message.
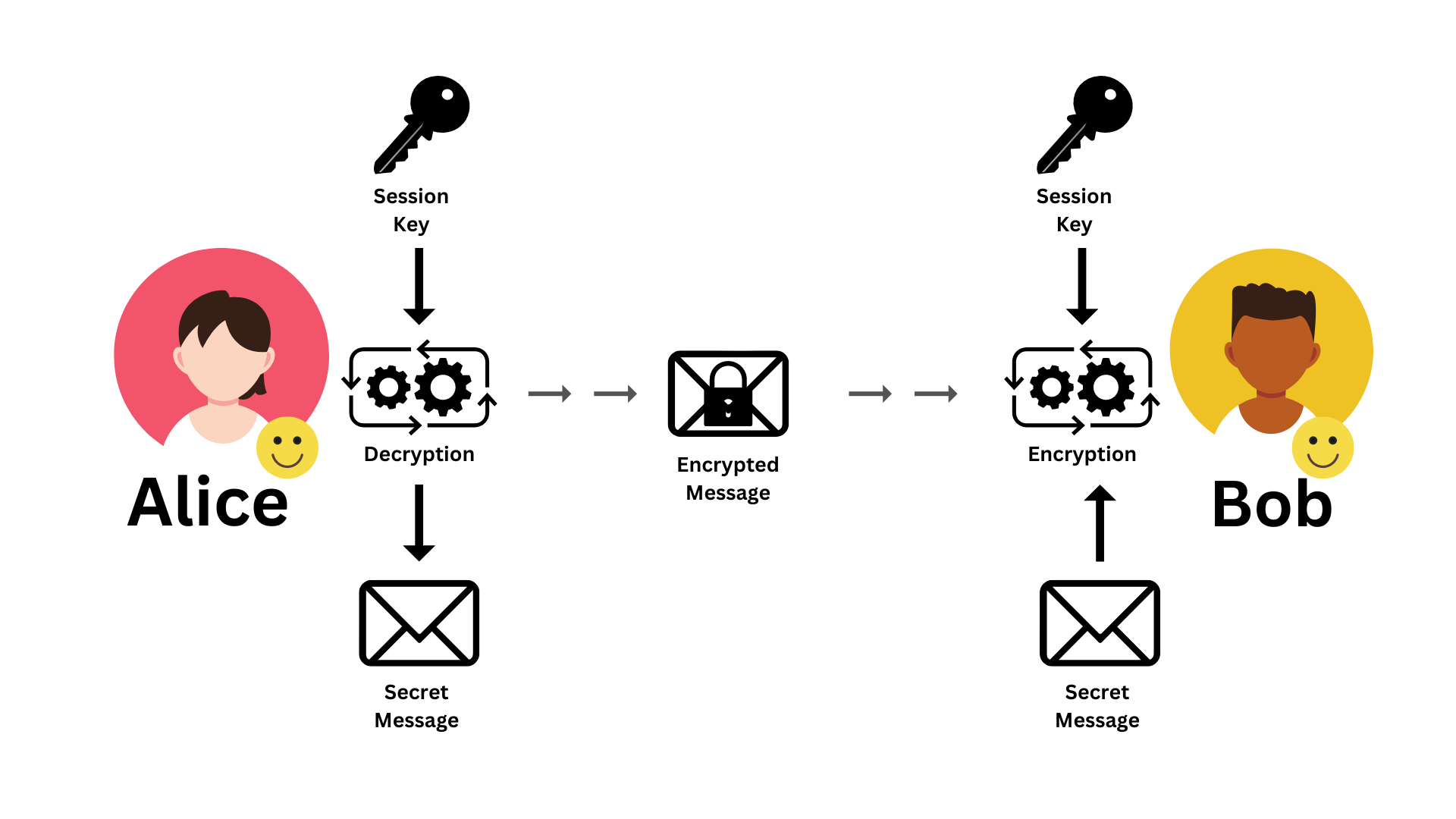
Diagram 05: Hybrid Encryption | Message from Bob to Alice
The communication in the other direction is also the same (Diagram 05). The only difference is, that Bob encrypts the message and Alice decrypts it. Other than that, the steps are exactly the same.
So, Why Hybrid Encryption?
As you know already, it’s more of a procedure of how you can utilize symmetric and asymmetric encryption together. You already see that it’s a process, then an algorithm like RSA or AES. So by using symmetric and asymmetric encryption schemas with this approach, we try to extract the advantages of them over the disadvantages they have.
For example, when we used symmetric encryption, we had a problem with key sharing. It was challenging to share keys over unsecured networks. And at the same time, it has a huge advantage over asymmetric encryption when it comes to strength and efficiency. But with asymmetric encryption, it was time and resource-consuming. So it was not good for encrypting big amounts of data and was less effective.
But the hybrid approach solves all those issues. It uses asymmetric encryption only for sharing the symmetric key. Once we establish the session, we can use symmetric encryption to continue the communication, so that we have a secure, effective communication channel.
Happy Reading ;)
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
 27 May 2024
27 May 2024 ![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)