Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
In the previous article series, we discussed the encryption and decryption processes. We know that encryption plays a crucial role in securing sensitive information from unauthorized access. In this article, we’ll look at the two fundamental methods of encryption : symmetric and asymmetric.
The main difference between symmetric and asymmetric encryption is the usage of the cryptographic keys. A particular algorithm is categorized under a given category by considering whether it uses the same key for encryption and decryption, or it needs two separate keys.
Symmetric Encryption
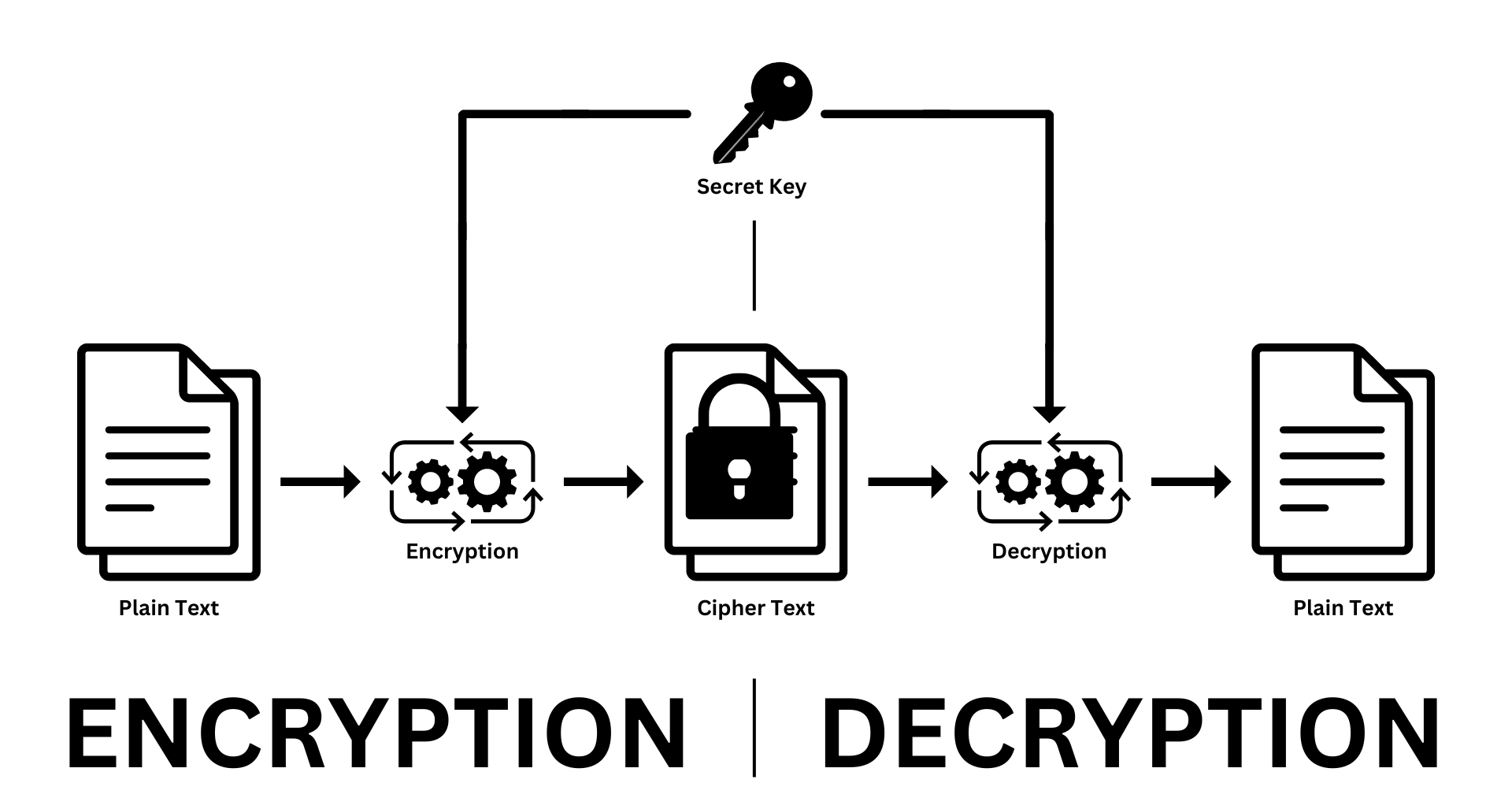
Diagram 01: Symmetric Encryption
Symmetric encryption, also known as secret-key, or single-key encryption, uses only a single key for both encryption and decryption processes. Both the sender and the recipient have to use the same key for the encryption and decryption process in this schema. The most widely used symmetric encryption algorithms are Advanced Encryption Standard (AES), Blowfish, Data Encryption Standard (DES), and Triple DES (3DES). If implemented correctly, AES is the most robust and highly secured algorithm among them.
Advantages
- Simplicity: Symmetric encryption is much more simple than asymmetric encryption. The process is very straightforward.
- Performance: Symmetric encryption is generally faster than asymmetric encryption. So this approach is very efficient and better for encrypting large amounts of data.
Disadvantages
- Key Distribution: Since symmetric encryption uses the same key for both encryption and decryption, both parties need to have this key. Sharing the secret key, however, can be challenging and is a main drawback. Fortunately, cryptology offers solutions to this problem, which we will discuss in upcoming articles
Special Note: Typically, symmetric encryption is defined as using the same key for both encryption and decryption. However, there are specific algorithms, like the Hill-Cipher , which are still considered symmetric even though the encryption and decryption keys are different. The reason is that one key can be easily derived from the other. In the Hill-Cipher, the encryption key is a matrix, and the decryption key is its inverse. Calculating the decryption key doesn't involve any secret or complex math problems, which is why it still falls under symmetric encryption.
Asymmetric Encryption
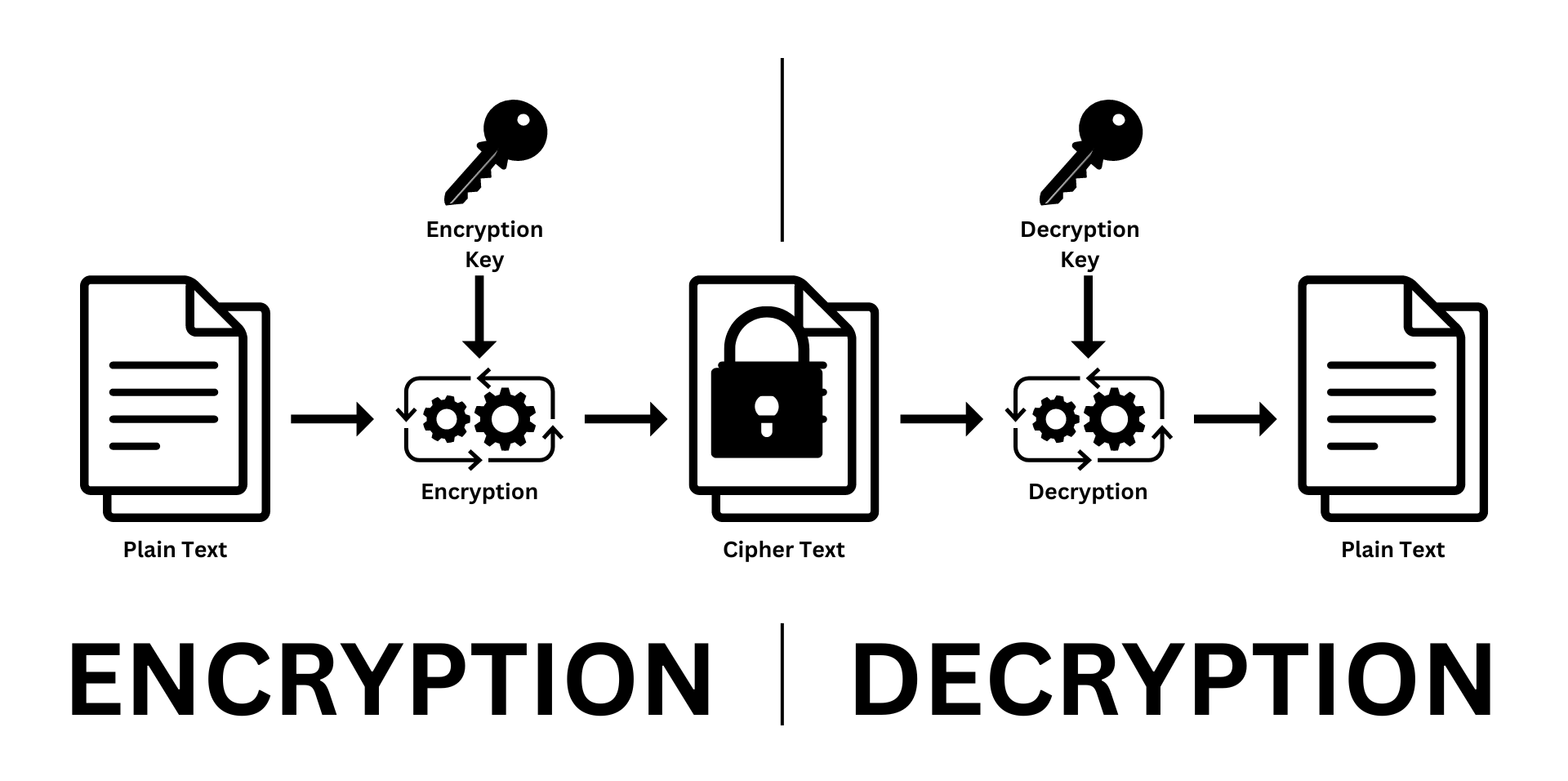
Diagram 02: Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, uses two different keys: one for encryption and one for decryption. These keys are called the public key and the private key, and they are mathematically linked. We’ll explore this more in upcoming articles.
As their names suggest, the public key tends to be publicly (freely) available for anyone who wishes to send an encrypted message to the key pair owner, while the private key is kept secure by the key pair owner.
The beauty of asymmetric encryption is that if you use one key for the encryption process, you have to use the other key for the decryption process. Imagine this :
- If you encrypt a message using the public key, you must use the matching private key to decrypt it. This is the most common scenario and we will discuss it more in the next article[Part 02].
- On the other hand, let’s say you encrypt the message with the private key. It can only be decrypted with the corresponding public key. This method is often used in digital signing. We will cover this concept in an upcoming article. Stay tuned!
The most commonly used asymmetric encryption algorithm is RSA.However, a newer algorithm called Elliptic Curve Cryptography (ECC) is becoming popular. ECC is more efficient and provides the same security strength as RSA but with shorter key lengths.
Advantages
- Secure Key Distribution: Unlike symmetric encryption, in asymmetric encryption the public key can be freely shared. So there’s no need for a secure method of sharing keys.
- Digital Signatures:With asymmetric encryption algorithms, we can create digital signatures. So other than ensuring confidentiality, we can use these algorithms to ensure authenticity and integrity as well.
Disadvantages
- Slow Performance: There are quite a bit of mathematical operations behind asymmetric encryptions than symmetric encryptions. So it’s much slower.
We've covered the basics of symmetric and asymmetric encryption. In the next article, we'll explore how these concepts are applied in the real world.
 27 May 2024
27 May 2024 ![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)