Introduction to Hashing: A Comprehensive Guide

Hashing is another key concept of cryptography. It takes input of any length and provides the output of a fixed length, and we call it hash value or hash digest.
Special Note: There are some hashing algorithms where the output size is not fixed.
So, hashing can be used to generate unique fingerprints for data. It is therefore excellent for quick comparisons, indexing, and data integrity checks.
The cool thing about hashing is that it's always the same. That is, the same input will always give the same output with the right hash algorithm.
Hashing is mainly used for password storage, password comparison, digital signatures, and data integrity checks.
How Hash Functions Work?
As you already know, hashing is all about converting the data into a fixed-size unique output.
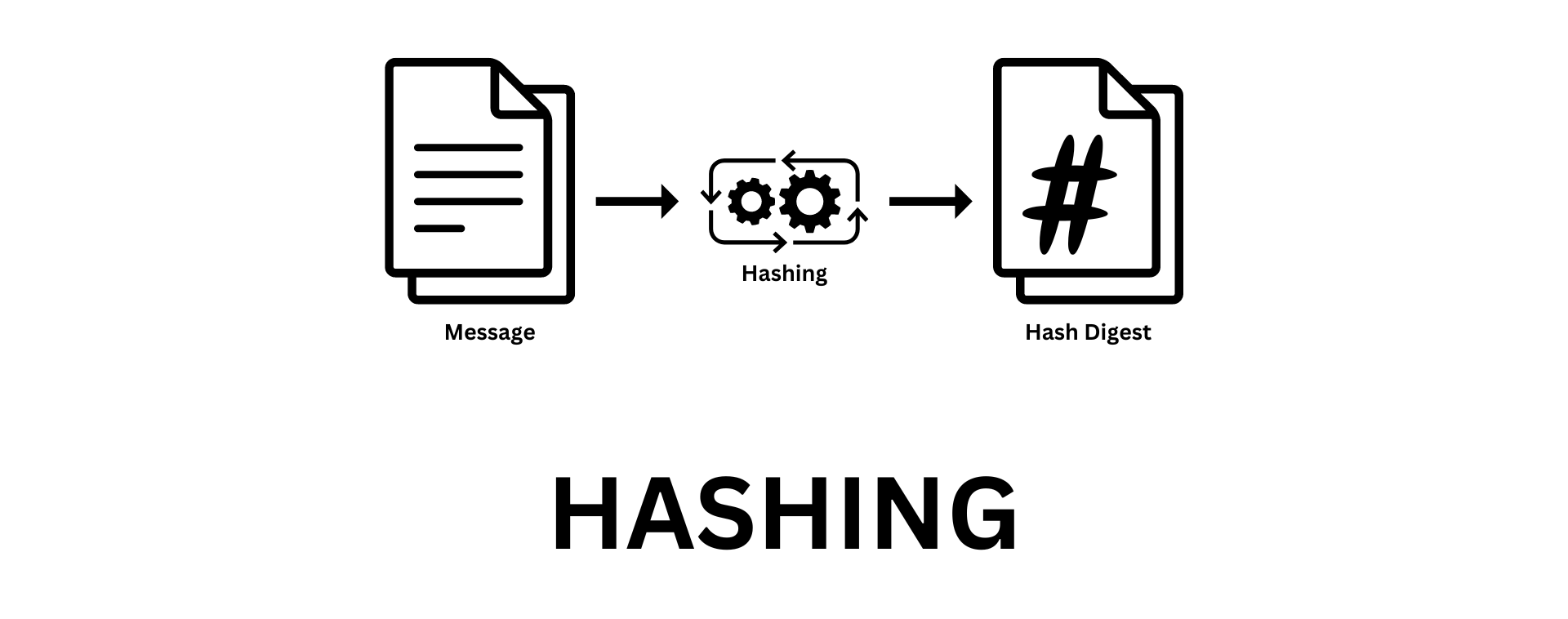
Diagram 01: hashing Process
The hashing process is simple. You just have to input the message or data you need to hash to the algorithm, and that’s it. Yep, it’s that simple.
The other important thing is, hashing is a one-way function, or we call it a trap-door function.
This means, you can generate the hash value of any message, but you can’t derive the original message from its hash value. There is no straight reverse approach for hashing.
The mathematical Beauty…
In most cases, hash functions use prime numbers, modular arithmetic, and the avalanche effect to achieve the goal mathematically. It utilizes those concepts to achieve faster calculation time and evenly distributed output without collisions.
If you change one full stop of a 1000-page book, the hash will be changed completely. Yep, it utilized mathematics that much.
This makes it hard for hackers to guess the original input from its hash.
These three principles build the base for creating secure hash functions. With prime numbers, modular arithmetic, and the avalanche effect, designers craft functions strong against attacks. This makes these tools vital for protecting our data.
Hashing in Action
Hashing is a key in many real-life uses. It helps with things like keeping passwords safe and checking if data changed from its original form.
We'll take a look at how hashing is used in these areas.
Secure Password Storage
When it comes to storing passwords, hash functions are very important. They make sure user passwords are safe. Even if a password database is hacked, the stored passwords are hard to backward-engineer.
This means they keep the original passwords secure.
Data Integrity Verification
Hashing also helps to keep data safe, both when it's stored or sent across networks. By checking if the hash value of the data received matches to the hash value expected, you can verify that the data was not changed. This keeps the data safe from tampering.
Version Control Systems
Certain systems like Git use hashing to keep track of code changes. Each code update is assigned a unique hash value. This hash value identifies that specific version of the code.
It helps developers manage changes and keep project files accurate.
Digital Forensics
Digital forensics relies on hashing to verify digital evidence. By hashing a digital file, investigators can confirm that it has not been altered.
This proof helps in legal cases, making the evidence more reliable.
And the list goes on…
Yeah, we have tons of applications, like, cryptocurrencies and blockchain technologies are heavily reliant on caching. You can utilize hashing with asymmetric encryption to achieve the digital signing process as we discussed in the previous article.
And hashing is super helpful in many places. From search engines and databases to caching systems and cybersecurity, they boost search performance. This makes them vital for handling big data and quick info processing.
Happy Reading :)
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
 27 May 2024
27 May 2024 ![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)