Introduction to Secret Splitting: A Comprehensive Guide

We discussed encryption, and how to utilize it to secure the secret by making them unreadable. But did you ever think about breaking your secret into several pieces?
Hold On? I am not talking about chunking your secret into 5 pieces and storing them in 5 different storages. This approach is much advanced, and it is called, Secret Splitting.
Understanding the Concept

Secret splitting is a way to make data safer. It breaks secrets such as encryption keys or passwords, into many pieces. These pieces go to different people or places, making it hard for one person to get the whole secret back.
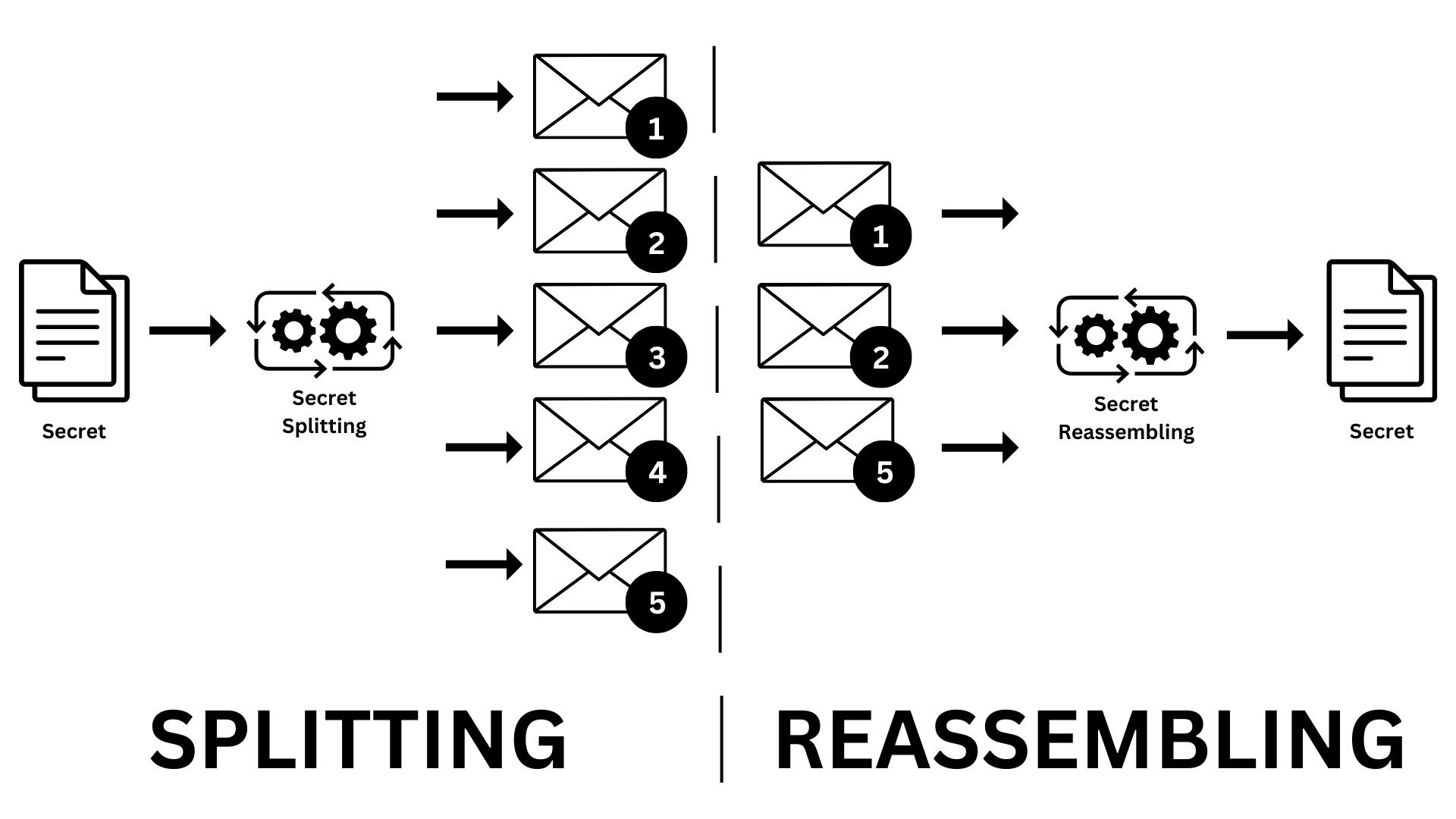
Diagram 01: Secret Splitting Process
But again, it’s not as simple as you think. There is advanced mathematics under the hood. It’s like, you can break your secret into n pieces using a particular secret splitting algorithm. We call this one piece a share.
But when you split them, you have to define how many shares are required for reassembling the original secret, let’s say you specified only n - 2 required. In that case, you need only n - 2 of these shares to get the original secret back.
For example, if you split the secret into 5 shares, you may only need 3 shares to reassemble it. Cool right :)
This method makes data much safer. If you spread the shares around, yet losing one won't mean losing everything. Even if an attacker gets some shares, he can't get the secret without the right number of them, in our case n - 2.
And more importantly, when sharing sensitive data, secret splitting makes sure no one person has all the info. This is great when different groups need to work together without risking data breaches. By breaking the data into shares, it's safe to share, and you can put it back together with the right number of parts.
Using secret splitting helps keep important data safe. It protects against unauthorized access and lowers the chance of data theft. This makes it a key part of keeping data secure.
Shamir’s Secret Sharing Algorithm
The art of secret splitting uses advanced techniques to keep sensitive data information safely. The most famous, and well-known one, Shamir's Secret Sharing Algorithm, was created in 1979.
- Shamir's Secret Sharing is super secure, even for someone with endless computer power.
- You can change how many shares you need to get the secret back.
- You can set up levels of trust with different shares, giving some people more power.
- Adding or changing shares won't mess up the original secret, making it easy to manage.
This method is mathematically based on polynomial interpolation over finite fields. We may discuss the mathematical implementation in a future article.
Secret Splitting in Practice

Secret splitting is mainly used to make assets safe by sharing sensitive info like encryption keys and passwords among several people, places, or communities. It is also useful for access control. It lets companies set strong rules for who can get to sensitive stuff.
For example, it can hide encryption keys or passwords, needing more than one person or device to unlock them. This makes systems much safer by stopping one person from being the only weak link. Probably you may see such scenarios in movies. :)
Secret splitting may be used even with digital signatures. You can share the signing key among several people, avoiding a single failure point and making signatures more reliable. Secure backup and recovery systems use secret splitting too, to make sure data can only be fully restored with the right number of parts, adding extra security.
Happy Reading :)
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
 27 May 2024
27 May 2024 ![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)