Introduction to Digital Signatures: A Comprehensive Guide

So far, we covered almost all the basic topics of cryptography in this series. But one more important topic is left to be discussed. Last, but not least, the topic for today's article is Digital Signatures.
Digital Signing is a mathematical technique for verifying digital messages or electronic documents. It’s widely used in various applications such as secure communication, digital product distribution, and financial transactions where it is required to ensure that the original content has not been altered or to verify who the sender of the content is.
How Digital Signing Works
If you remember, we already discussed that we can utilize asymmetric encryption for digital signing in the previous articles. The difference is just the way of utilizing keys.
Digital signing has two main processes. The first process is to generate a unique digital fingerprint of the message or document. The other process is to verify the fingerprint and make sure that the message or the document is not altered.
For instance, Alice is going to send a message to Bob over an insecure network. They need to verify that the message is not altered between the transmission, and also Bob needs to make sure that the particular message is from Alice.
So, Alice and Bob decide to utilize digital signing to fulfill their requirement.
Prerequisites
As usual, the person who sends the file should decide the asymmetric encryption algorithm to use and should generate a key pair. Then she keeps his private key secret, without exposing it, and makes her public key publicly available.
Create Digital Signature
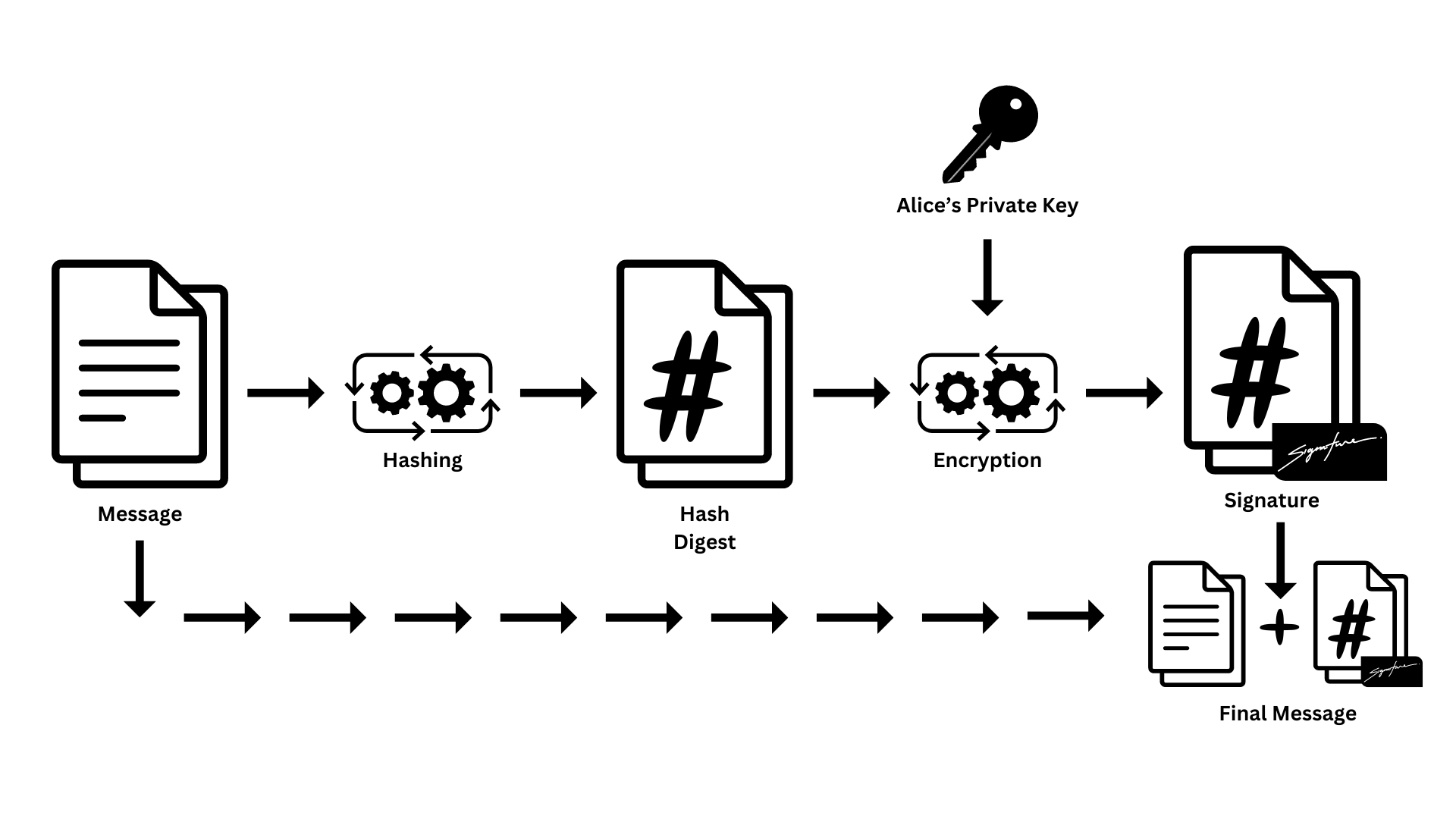
Diagram 01: Signing Process
Steps to create the digital signature are forward.
- First Alice hashes her message and generates the hash value of it.
- Then she encrypts the hashed value with her private key.
- Then Alice sends the original message and the digital signature to Bob.
Special Note: This encrypted hashed value of the message is called the Digital Signature.
Verifying the Digital Signature
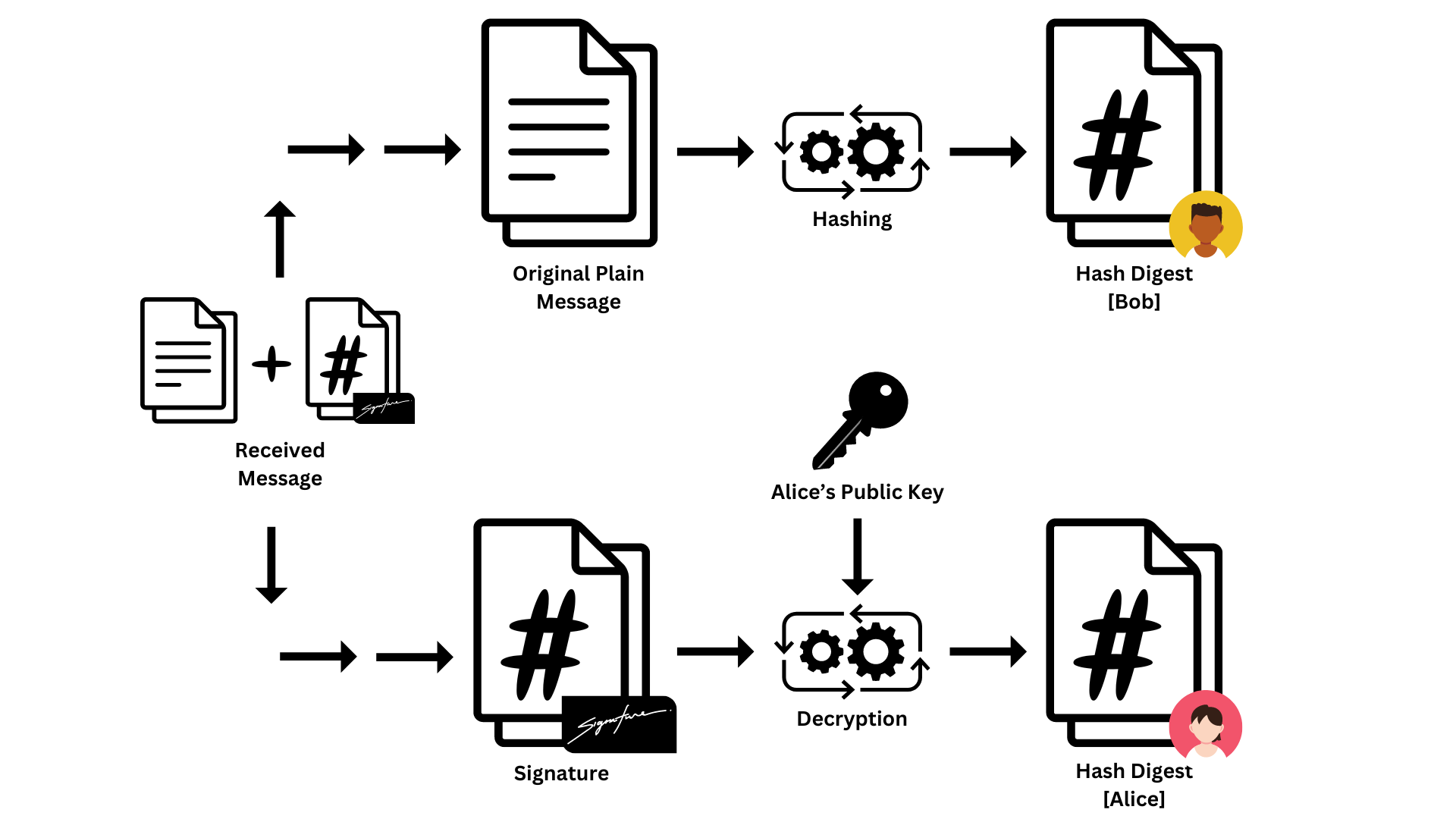
Diagram 02: Verifying Process
Steps to verify digital signature are as below.
- Bob takes Alice's original message, then hashes it, and generates the hashed value (let's say HA).
- Then he decrypts the digital signature Alice sent with Alice’s public key and obtains the hashed value Alice calculated (let's say HA).
- Then Bob compares HA and HB. If they are equal, it means that the message is not altered in the transmission and also originally sent by Alice.
Benefits and Applications
The main benefits of digital signing are security and authenticity. It can be used to ensure the integrity of the message and the identity of the sender. Further, it can be used to streamline the document workflow and reduce the necessity of the physical signatures.
Also, digital signatures are commonly used in business and commercial transactions, especially to ensure the authenticity of contracts, agreements, and financial documents.
Happy Reading :)
![Symmetric vs Asymmetric Encryption [Part 01]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-26.png)
 27 May 2024
27 May 2024 ![Symmetric vs Asymmetric Encryption [Part 02]: Understanding the Differences](https://codimite.ai/wp-content/uploads/Blog-cover-22.png)