Introduction to Encryption [Part 02] : Understanding the Basics – Use Cases
![Introduction to Encryption [Part 02] : Understanding the Basics – Use Cases](https://codimite.ai/wp-content/uploads/Blog-Cover-13.png)
In the previous article Part 01, we covered the theories about encryption and decryption. But just learning theories without understanding use cases is useless. So the focus of this article is to explain why we need encryption, and what will happen without it.
In a world without Encryption…
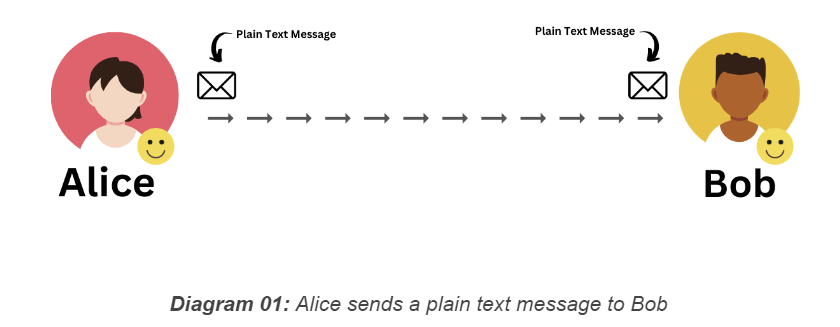
Meet Alice and Bob. Alice has a super secret message she wants to share with Bob. So, she sends it to him through a network that isn't secure. When Bob gets the message, he can easily read it, and now he knows the super secret message that is ‘Both Alice and Bob are happy.’
BUT! What’s the issue?
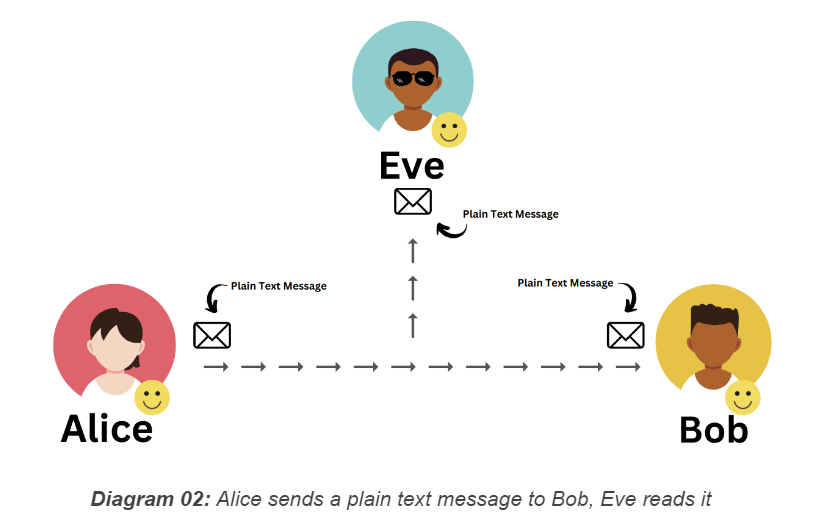
Remember, we're sending this message through a channel that isn't safe, meaning anyone can listen in. Let me introduce Eve, the eavesdropper in this scenario. Because the channel isn't secure, Eve might have intercepted the super secret message Alice sent and could easily read it since it's in plain text. In the end, Alice's super secret message is revealed to Eve, the attacker, which is bad news. And not only Alice and Bob, but even Eve is happy at the end.
Encryption Safeguards Confidentiality…
Alice and Bob want to keep their messages private, so they decide to use encryption.
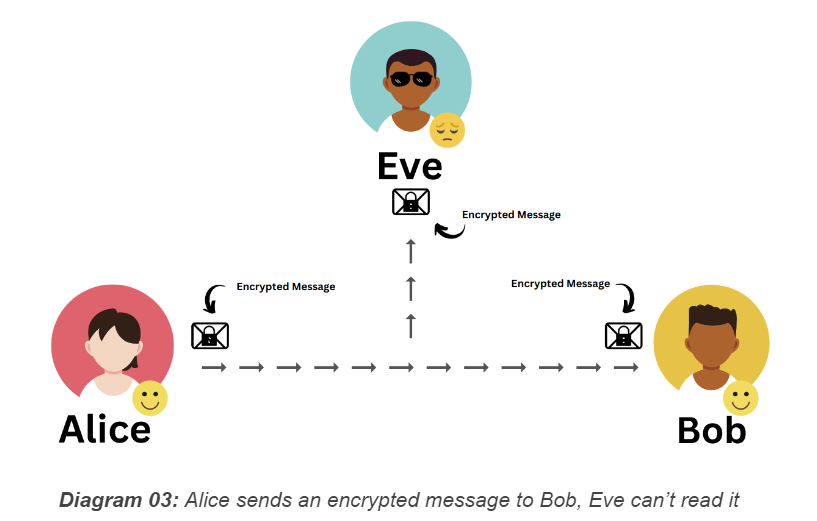
They agree on an encryption algorithm and share keys. Alice encrypts her super secret message and sends it over the unsecured channel. Even though Eve tries to intercept it, she can't understand the encrypted message without the key. Only Bob can decrypt it and read the original message. Thanks to encryption, Alice and Bob safely share their secret without Eve snooping in. Alice and Bob are happy, but Eve is left out this time.