Unlocking Microsoft 365 with Microsoft Graph API: A Guide to Integration and Authentication

Microsoft Graph API is the gateway to accessing and managing data from Microsoft 365 services, making it a key tool for developers and IT professionals. Whether you're building an internal app to manage users or creating automation workflows, Microsoft Graph provides a unified API endpoint to connect with a variety of Microsoft services like Azure Active Directory, Outlook, SharePoint, OneDrive, and Microsoft Teams. In this post, we will explore two essential aspects: an introduction to the Graph API and how to securely authenticate and authorize access using Azure AD.
Introduction to Microsoft Graph API
Microsoft Graph API offers a single API endpoint that connects to the diverse ecosystem of Microsoft 365 services. This enables developers to programmatically interact with an organization’s data, providing access to resources like users, files, emails, calendars, and more. It simplifies integration, allowing apps to communicate seamlessly across different Microsoft products using a unified API.
Why Use Microsoft Graph API?
- Unified Access: Microsoft Graph API consolidates many different Microsoft service APIs into one, allowing developers to access information from Outlook, SharePoint, Teams, and more through a single interface.
- Real-Time Data: It supports real-time access to data such as email notifications, calendar events, and user status. This allows developers to build responsive applications that update dynamically as new information arrives.
- Wide Reach: Whether you're managing enterprise-level resources like users and devices in Azure AD or collaborating with documents in SharePoint, Microsoft Graph API gives you broad access to Microsoft services.
- Automation: Graph API can streamline processes by enabling automation across Microsoft 365 apps. It provides functionality to automate user creation, handle calendar events, or even manage resources within Microsoft Teams.
The breadth of access Microsoft Graph API offers makes it a cornerstone for app developers looking to build solutions that integrate deeply with Microsoft 365.
Authentication and Authorization with Microsoft Graph API
Securing access to Microsoft Graph is an important step in interacting with Microsoft 365 data. Like most modern APIs, Microsoft Graph uses OAuth 2.0 to authenticate requests, ensuring secure access to organizational data while granting different permission levels depending on user needs.
Setting Up OAuth 2.0 Authentication
OAuth 2.0 is the primary method for authenticating to Microsoft Graph. It allows applications to request permission on behalf of a user or an organization. Azure Active Directory (Azure AD) plays a central role in the authentication process by controlling access to Microsoft Graph.
Here are the key steps involved in setting up OAuth 2.0:
- Register an Application in Azure AD:
The first step is registering your application in Azure AD. This provides you with a client ID and secret, which you will use when requesting access tokens. You can register an app in the Azure Portal by going to App registrations and creating a new application. - Granting Permissions:
Once the app is registered, you'll need to assign permissions. Microsoft Graph has a wide range of permissions, categorized as delegated (acting on behalf of a user) or application (independent of user context). The permissions should align with the specific tasks your application needs to perform. - Obtain an Access Token:
After registration, your app can request an OAuth token. This token is essential for making API calls to Microsoft Graph. Depending on the permission type, the process will vary slightly:
- Delegated Permissions: The user needs to authenticate, and the app receives a token to act on their behalf.
- Application Permissions: The app is authenticated without user intervention, suitable for background services or automation tasks.
- Call Microsoft Graph API:With the access token in hand, the application can now make requests to the Microsoft Graph API. The token will be sent as a bearer token in the Authorization header of HTTP requests, granting access to the necessary data.
Managing Permissions and Least Privilege Access
When setting up OAuth for Microsoft Graph, it's important to adopt a principle of least privilege—granting only the permissions your app needs. Microsoft Graph organizes its permissions into specific scopes, which developers can specify when requesting access tokens. This is essential for ensuring that your application does not overreach in terms of access to sensitive data.
- User.Read: Basic read-only access to a user’s profile.
- Mail.Read: Read-only access to a user's emails.
- User.ReadWrite.All: Full read-write access to all users in a directory (suitable for admin-level apps).
This fine-grained control over permissions helps to mitigate security risks by ensuring that the app has only the necessary access.
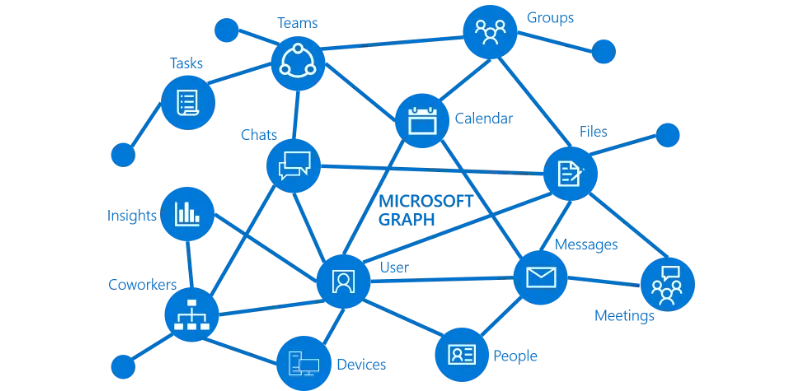
When working with Microsoft Graph API, there are several other important factors to consider beyond authentication and authorization:
- Rate Limits - Microsoft Graph imposes rate limits to prevent abuse and ensure fair use of resources. Exceeding these limits results in "429 Too Many Requests" responses.
- API Versioning:Microsoft Graph supports multiple versions (e.g., v1.0 and beta). While the beta version provides access to the latest features, it is not stable and may change.
- Permission Best Practices:Always follow the principle of least privilege when requesting permissions for your app.
- Error Handling:Robust error handling is essential. Microsoft Graph can return various error codes (such as 400 for bad requests or 503 for service unavailability).
- Security Best Practices:Secure your access tokens by storing them securely and refreshing them only when needed. Additionally, monitor for unauthorized access and revoke permissions when no longer necessary.
Conclusion
Microsoft Graph API is a powerful tool for accessing Microsoft 365 data, providing developers with a single endpoint to connect with a range of services. The integration process involves securing access via OAuth 2.0, ensuring that only authorized applications can access the appropriate data. By understanding how to authenticate and authorize your applications, you can build robust and secure solutions that take full advantage of the Microsoft 365 ecosystem.
By using Microsoft Graph API with proper authentication, you ensure secure, scalable, and productive applications that can drive business automation and intelligence.