Isolated Web Apps (IWAs): A New Era of Web Security

Understanding Isolated Web Apps
Isolated Web Apps (IWAs) represent a significant advancement in web security and privacy. They are designed to operate in a sandboxed environment, separating them from the main browser process and other web applications. This isolation ensures that potential vulnerabilities or malicious code within one IWA cannot compromise the security of others or the underlying system.
Key Features of IWAs
1. Sandboxed Environment:
- IWAs run in a separate process, limiting their access to system resources and preventing them from interfering with other applications or the operating system.
- This isolation reduces the risk of attacks like cross-site scripting (XSS) and cross-site request forgery (CSRF).
- For instance, Google Chrome's Site Isolation feature demonstrates a real-world application of similar principles. By isolating each website in a separate process, Chrome ensures that malicious sites cannot access sensitive data from other open tabs or browser sessions. This has been particularly effective in mitigating threats like Spectre and Meltdown attacks, which exploit vulnerabilities in modern processors.
2. Restricted Permissions:
- IWAs have limited permissions, such as file system access and network connectivity. This minimizes the potential damage that can be caused by malicious code.
3. Enhanced Privacy:
- By operating in a separate process, IWAs can better protect user privacy. They can limit data sharing between different websites and prevent tracking across multiple tabs or windows.
4. Improved Performance:
- In some cases, IWAs can improve performance by offloading resource-intensive tasks to separate processes. This can lead to faster loading times and smoother user experiences.
How IWAs Benefit Users
- Enhanced Security: IWAs provide a more secure browsing experience by reducing the attack surface and mitigating the impact of potential vulnerabilities.
- Improved Privacy: By limiting data sharing and tracking, IWAs can help protect user privacy.
- Better Performance: In certain scenarios, IWAs can lead to faster and more responsive web applications.
The Future of Web Security
IWAs are a promising technology that has the potential to revolutionize web security and privacy. As browser vendors continue to invest in IWA development, we can expect to see more advanced features and improved performance in the future.
While IWAs offer significant benefits, it's important to note that they are not a silver bullet. Users should still practice good security habits, such as using strong passwords, avoiding suspicious websites, and keeping their software up-to-date.
By understanding the principles behind IWAs and adopting best practices, users can significantly enhance their online security and privacy.
Configuring Isolated Web Apps (IWAs): A General Overview
Note: The specific configuration steps for IWAs can vary significantly depending on the browser, operating system, and the particular IWA implementation. However, here's a general overview of the key considerations and potential approaches:
Browser-Level Configuration
1. Enable IWA Support:
- Chrome: While Chrome doesn't have direct IWA support, you can explore experimental features or use extensions to enhance security and privacy.
- Firefox: Firefox supports Site Isolation, which is similar to IWA. You can enable it in the browser's settings to isolate different websites.
- Edge: Microsoft Edge supports Site Isolation and other security features that can be configured in the browser settings.
2. Configure IWA Policies:
- Some browsers allow you to customize IWA policies to control how websites are isolated and what permissions they have.
- This might involve setting up rules for specific domains or categories of websites.
Operating System-Level Configuration
1. Configure Windows Security Policies:
- If your IWA solution relies on Windows security policies, you may need to adjust Group Policy settings to control user access and application behavior.
- This could involve configuring application control policies, user rights assignments, and other security settings.
2. Configure Network Security:
- Network security policies can be used to restrict network access for IWA applications, ensuring they only communicate with authorized servers.
- This might involve using firewalls, network segmentation, or other network security measures.
Application-Level Configuration
1. Deploy IWA Applications:
- Deploy the IWA applications to your servers or cloud infrastructure.
- Configure the applications to use the appropriate security settings and authentication mechanisms.
2. Configure IWA Settings:
- Configure the IWA settings within the application to control how it interacts with the browser and the operating system.
- This might involve setting up authentication methods, defining security policies, and configuring access controls.
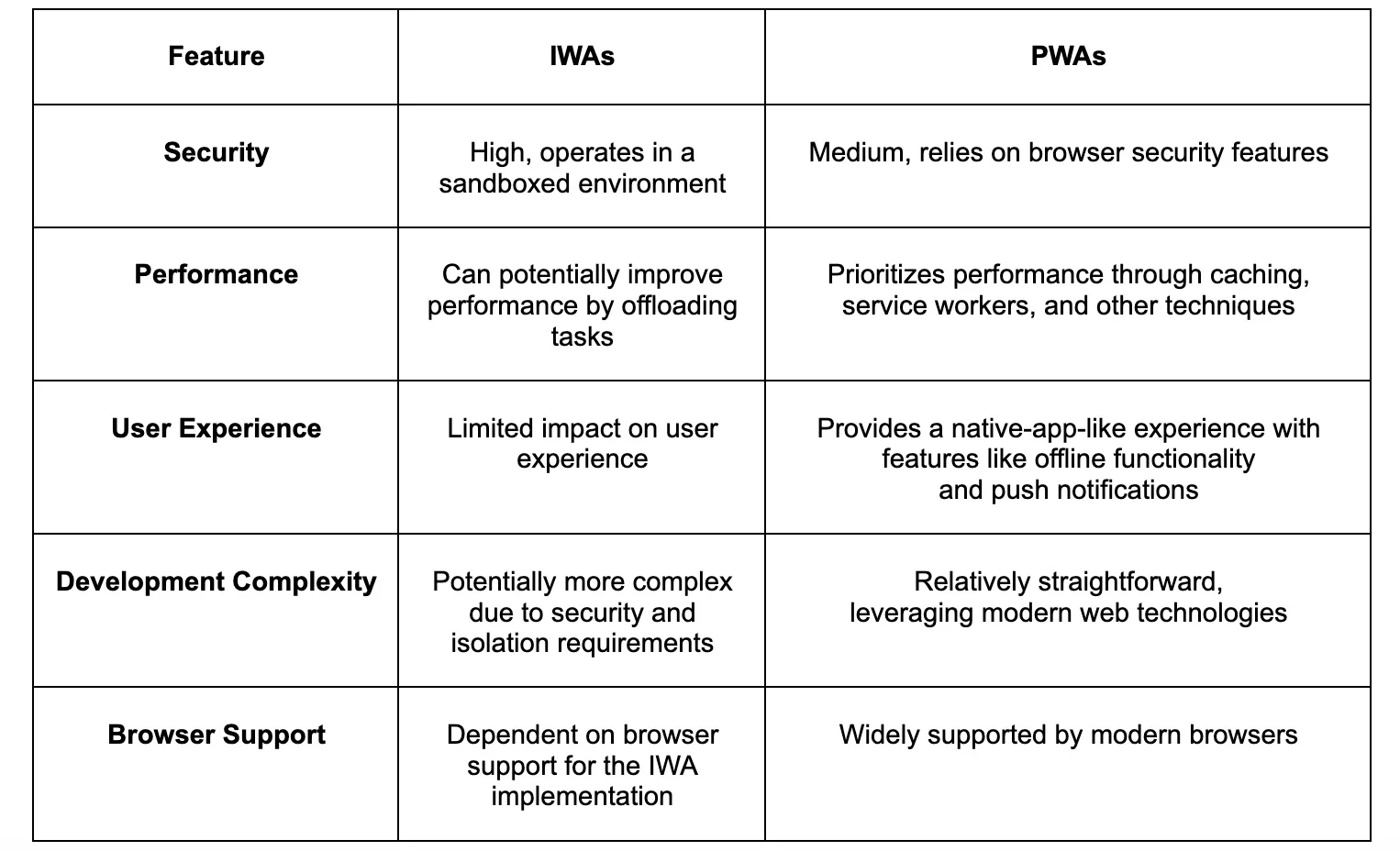
Comparing IWAs and PWAs
While both Isolated Web Apps (IWAs) and Progressive Web Apps (PWAs) aim to enhance the web experience, they differ significantly in their core concepts and objectives. Let's delve into a comparative analysis:
Core Concepts
- IWAs: Focus on security and isolation. They operate in a sandboxed environment, separating them from the main browser process and other web applications. This isolation ensures that potential vulnerabilities or malicious code within one IWA cannot compromise the security of others or the underlying system.
- PWAs: Prioritize performance and user experience. They leverage modern web technologies to provide a native-app-like experience, including features like offline functionality, push notifications, and fast loading times.
Key Differences
Conclusion
In conclusion, Isolated Web Apps (IWAs) represent a significant stride in enhancing web security and privacy. By operating in a sandboxed environment, IWAs mitigate the risks associated with malicious code and unauthorized access, providing a more secure browsing experience.
While the potential benefits of IWAs are substantial, their widespread adoption and effectiveness depend on various factors, including browser compatibility, operating system support, and the willingness of web developers to embrace this technology. As browser vendors continue to invest in IWA development, we can anticipate further advancements in web security and privacy.
It is crucial to remember that IWAs are not a panacea. Users should continue to practice good security habits, such as using strong passwords, avoiding suspicious websites, and keeping their software up-to-date. By combining the power of IWAs with responsible online behavior, we can significantly enhance our digital security posture.